Hello, cloud explorers! 👋 Ever wondered how to keep your Google Cloud Platform (GCP) resources secure while ensuring the right people have access? Welcome to the world of Google Cloud Identity and Access Management (IAM)! Let’s dive into this essential service that helps you manage who can do what on your GCP resources. Ready? Let’s get started! 🚀

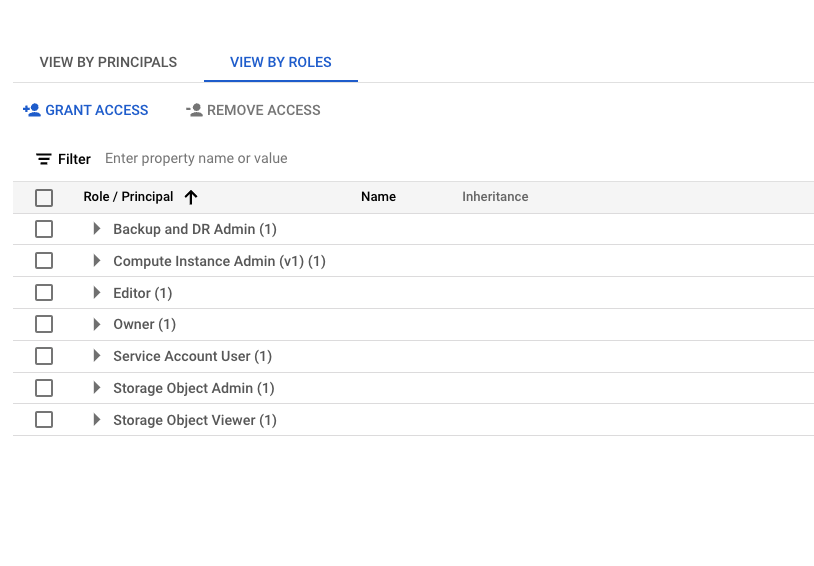
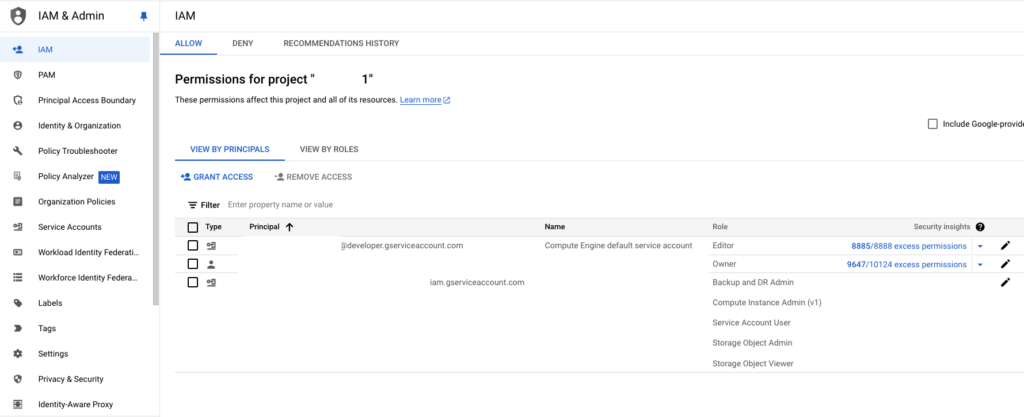
The GCP IAM dashboard showing users, roles, and permissions.
What is Google Cloud IAM? 🤔
Google Cloud IAM is a unified system for managing access to resources in GCP. It allows you to grant granular access to specific resources and prevents unauthorized access to others. Think of it as the security guard of your cloud environment, making sure only the right people get in. 🛡️
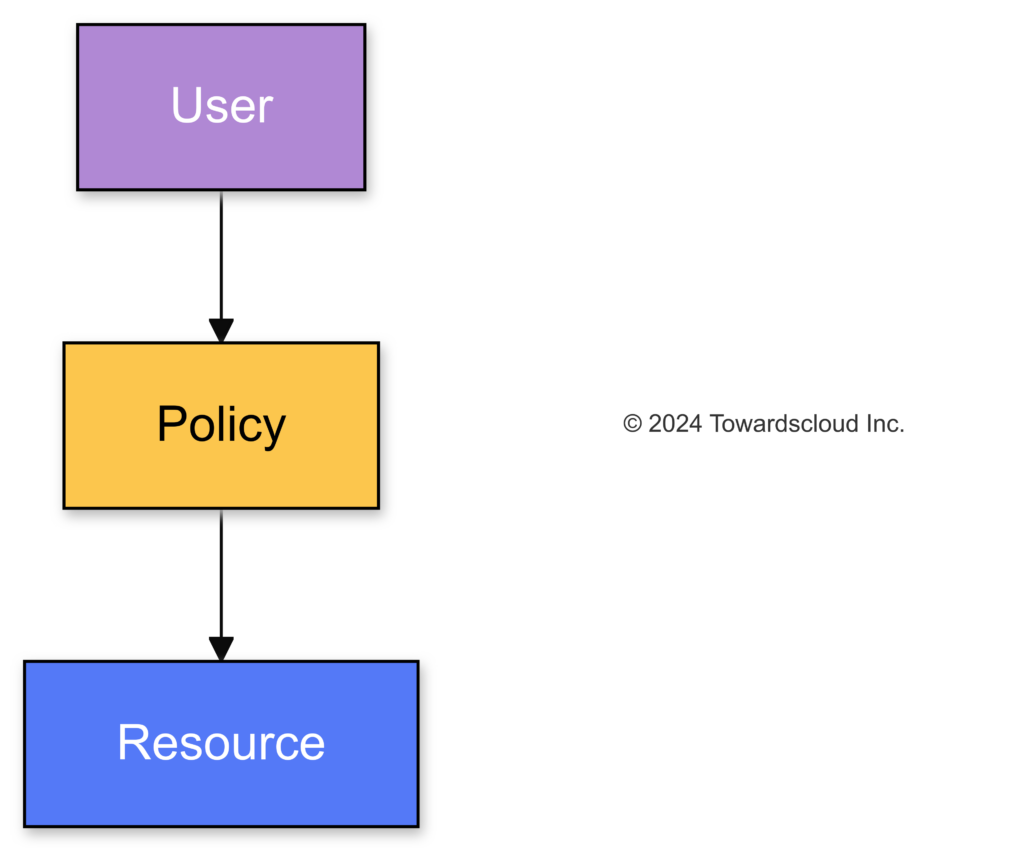
A user accesses a resource through a policy
Key Concepts of GCP IAM 📚
Understanding IAM involves getting familiar with its core components:
1. Members 👥
Members are entities that can perform actions on your GCP resources. They can be:
- Google Accounts: Individual users with a Google email.
- Service Accounts: Accounts used by applications or VMs.
- Google Groups: A group of Google accounts.
- Domains: All the users in a G Suite or Cloud Identity domain.
2. Roles 🎭
Roles define what permissions a member has. There are three types:
- Primitive Roles: Basic roles like Owner, Editor, and Viewer.
- Predefined Roles: Fine-grained roles for specific services.
- Custom Roles: Roles you create with a set of permissions you define.
3. Permissions ✅
Permissions are what allow members to perform specific actions on resources, like compute.instances.start or storage.buckets.list.
4. Policies 📜
Policies bind members to roles. They are attached to resources and define who has what access to which resource.
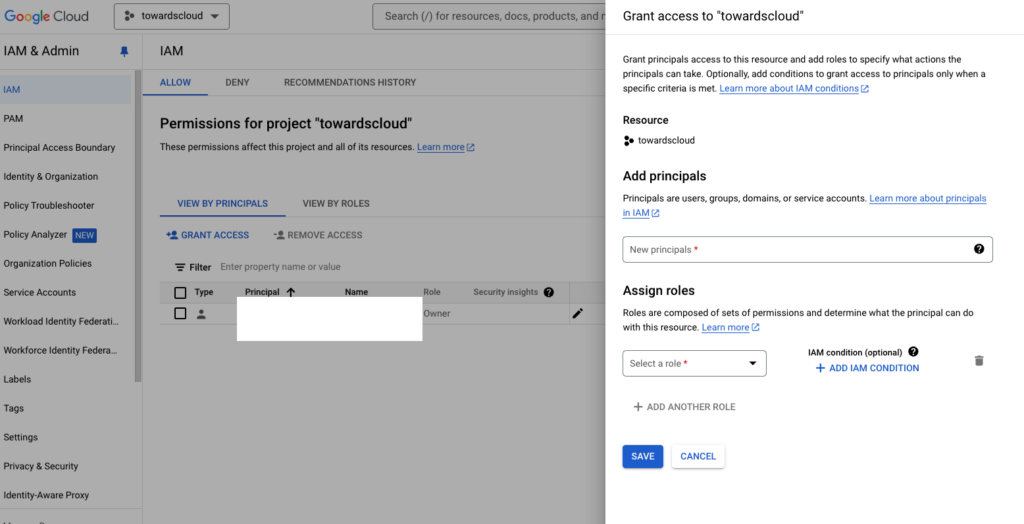
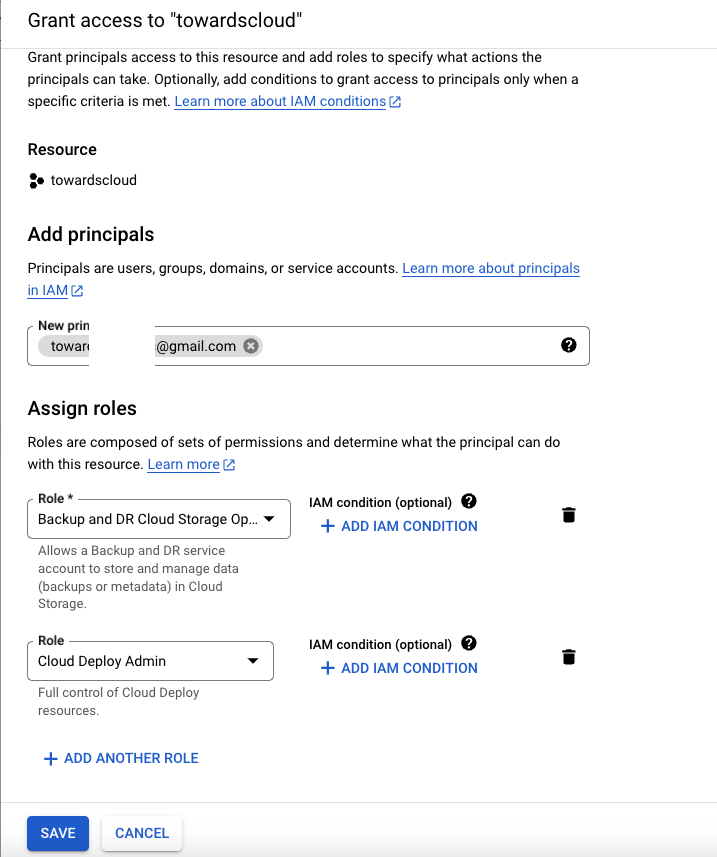
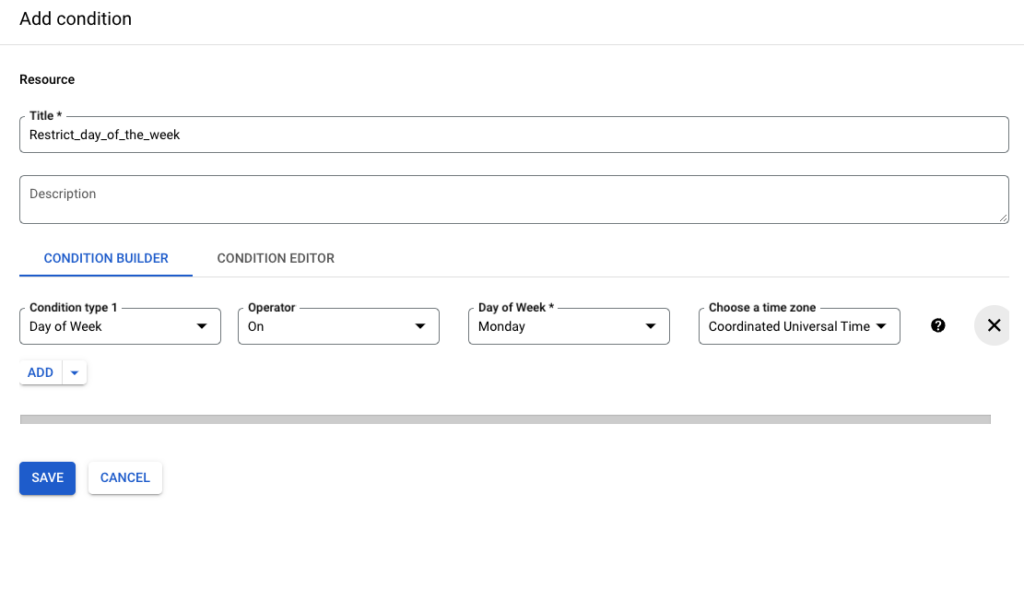
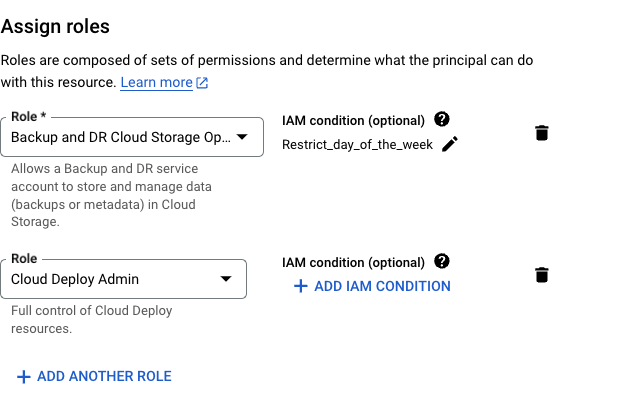
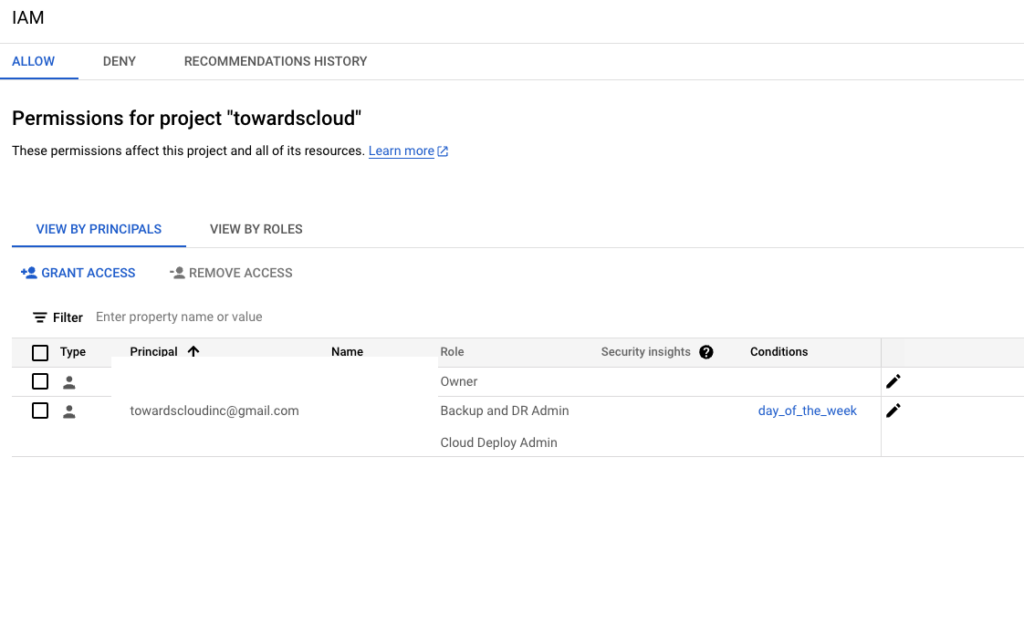
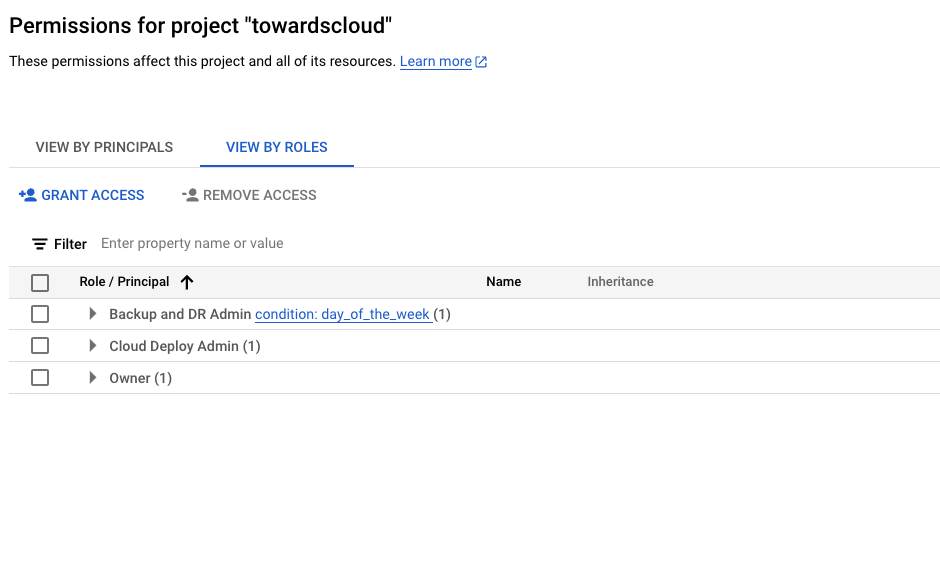
Example of an IAM policy binding showing a member assigned to a role.
How GCP IAM Works ⚙️
At its core, IAM controls access through authentication and authorization.
Authentication 🔑
- Who are you?
- Users authenticate using their Google credentials.
- Service accounts authenticate using keys.
Authorization ✔️
- What can you do?
- After authentication, IAM checks if the user has the necessary permissions.
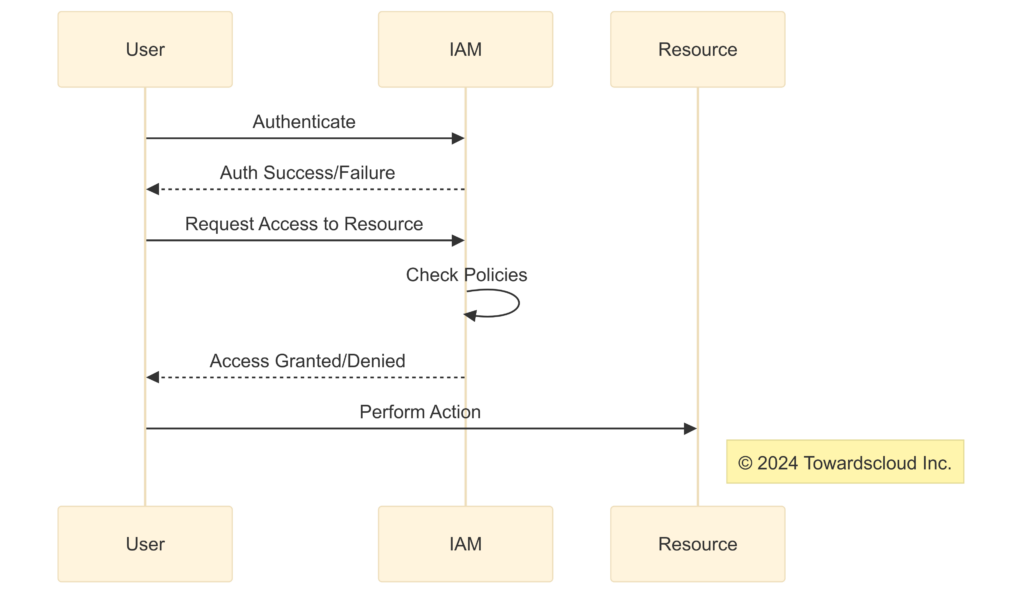
Sequence of authentication and authorization in GCP IAM
Managing Access with GCP IAM 🛠️
Assigning Roles to Members 🎯
To grant access:
- Identify the Member: User, service account, etc.
- Select the Role: Determine the level of access required.
- Bind the Role to the Member: Attach the role to the member for a specific resource.
Example: Granting a developer the roles/compute.instanceAdmin role to manage VM instances.
Custom Roles 🧩
Custom roles allow you to create a set of permissions tailored to your needs.
- Why Use Custom Roles? For the principle of least privilege—granting only the permissions necessary.
- How to Create?
- Navigate to IAM & Admin > Roles.
- Click “Create Role”.
- Define permissions.
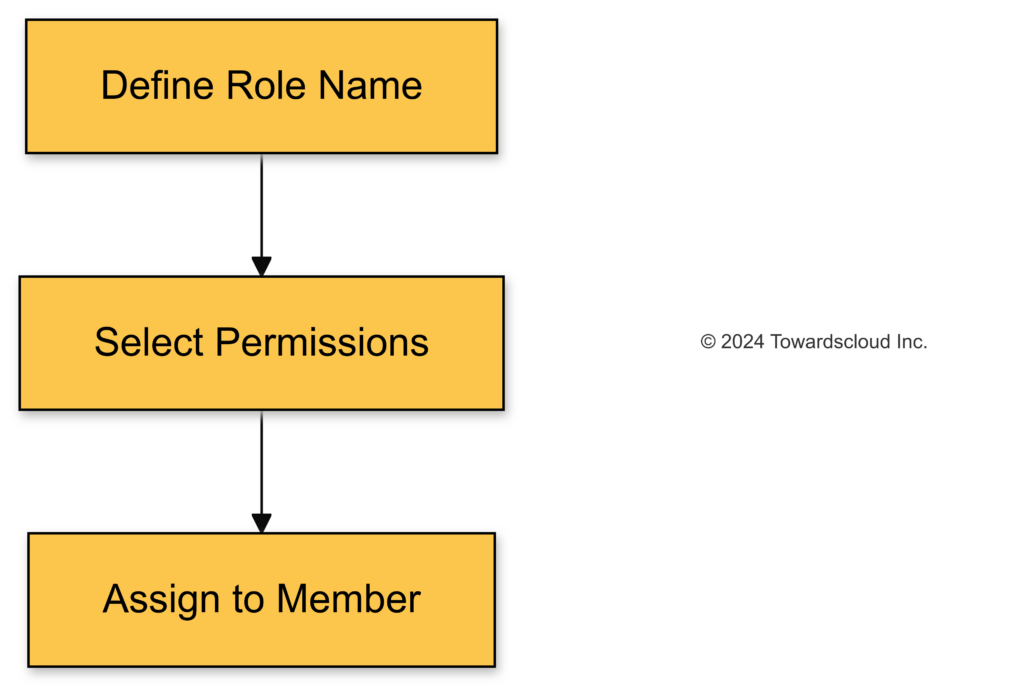
Steps to create a custom role.
Best Practices for GCP IAM 🌟
- Follow the Principle of Least Privilege: Grant the minimal required permissions.
- Use Predefined Roles When Possible: They are maintained by Google and updated automatically.
- Regularly Audit IAM Policies: Ensure that access levels are still appropriate.
- Use Groups for Access Control: Easier to manage than individual accounts.
- Monitor with Cloud Audit Logs: Track who did what and when.
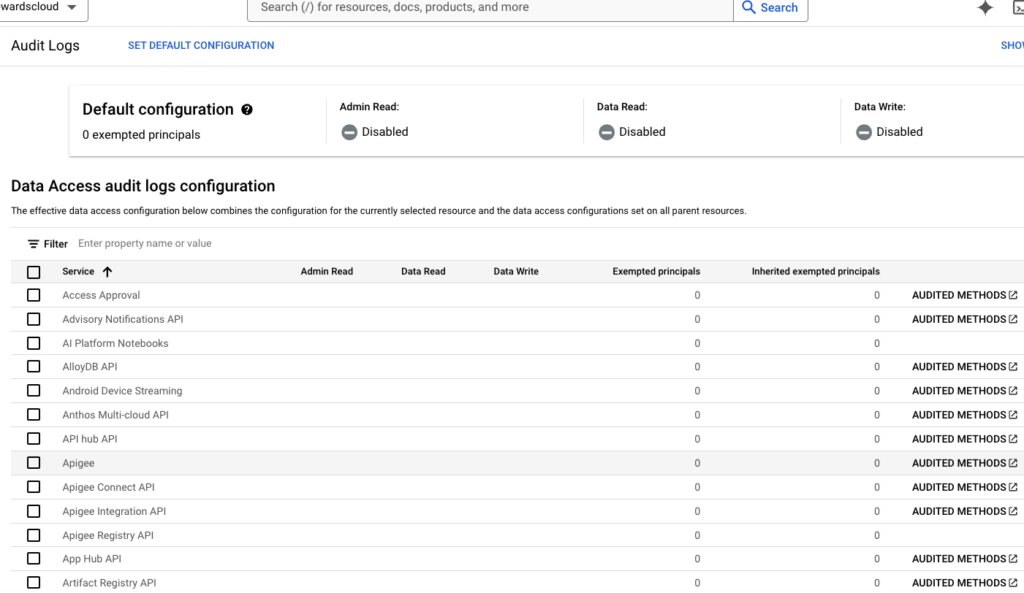
Viewing IAM changes in Cloud Audit Logs.
Real-World Scenarios 🌍
Scenario 1: Secure Application Deployment 🚀
- Problem: You have a team of developers who need to deploy applications but shouldn’t have access to billing information.
- Solution: Assign the
roles/appengine.deployerrole to the developers.
Scenario 2: Limited Storage Access 📦
- Problem: An external contractor needs access to a specific Cloud Storage bucket.
- Solution: Create a custom role with permissions only for that bucket and assign it to the contractor.
Scenario 3: Service Account for Automation 🤖
- Problem: An automated script needs to start and stop VM instances.
- Solution: Create a service account with the
roles/compute.instanceAdminrole and use it in your script.
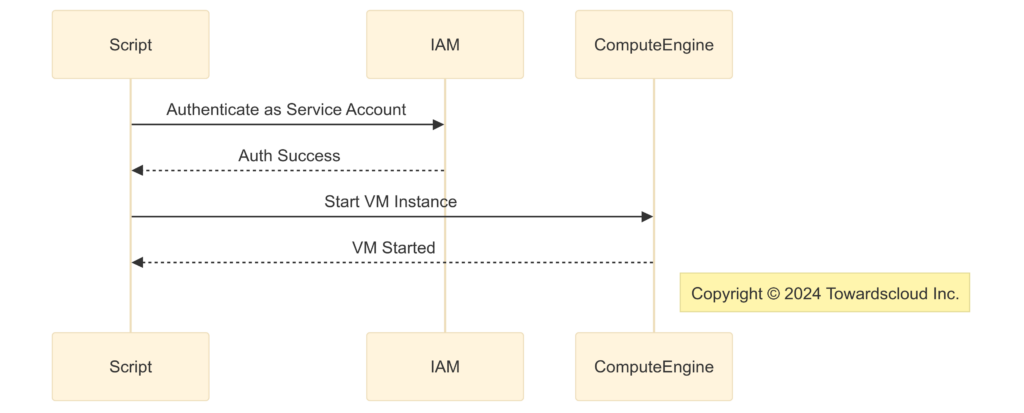
Service account automating VM instance operations.
IAM and Resource Hierarchy 🌲
GCP resources are organized hierarchically:
- Organization: The root node.
- Folders: Group projects or other folders.
- Projects: Container for resources.
- Resources: Individual services like VM instances.
Policies can be applied at any level and are inherited by lower levels.
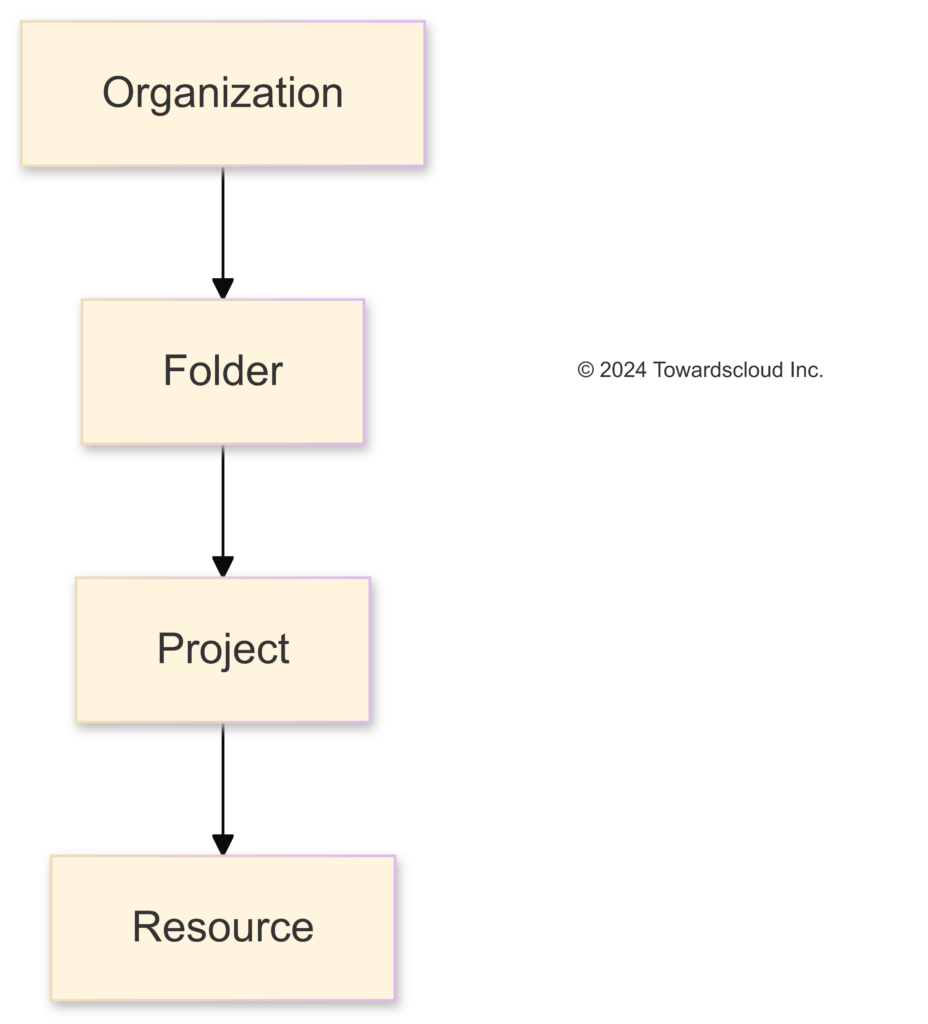
GCP resource hierarchy.
Tips and Tricks 🎩
- Use IAM Recommender: Suggests role modifications based on usage.
- Set up Conditional Access: Policies that grant access under certain conditions.
- Implement Two-Factor Authentication: Adds an extra layer of security.
IAM Recommender.
Conclusion 🎉
GCP IAM is a powerful tool that, when used correctly, ensures your cloud environment is both secure and efficient. By understanding its components and best practices, you can confidently manage access to your resources.
Ready to take control of your cloud security? Dive into GCP IAM and start implementing these practices today! 🔐☁️
Happy Cloud Securing! 🌥️🔒